A Virtual Private Network (VPN) is the overlay of a private network over a public or shared network. Data can be sent from a remote computing device to other devices connected to the private network and therefore services provided by the private network are accessible from the remote locations. In order to access the private network over a public/shared network, the data from a remote computer must traverse the public/shared network in a secure manner to ensure confidentiality of information and security of the private/shared network.
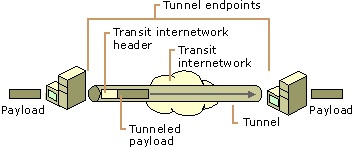
The IP data packet is encrypted and encapsulated in another IP header. The encapsulating header creates a VPN tunnel between the remote computing device and the private network. The encryption key to decrypt the inner header and the data are available with the endpoints only. The encrypted packet inside the public IP header is the VPN connection between the remote computing device and the private network. The VPN connection thus provides a facility to access the corporate private network with a point-to-point connection from any remote location irrespective of how the tunnel is configured. The remote user or branch office may subscribe to a local ISP or may have a dedicated dial-up connection with the corporate office. The tunneling protocols used are Point-to-Point Tunneling Protocol (PPTP), Layer Two Tunneling Protocol (L2TP) and IPSec tunnel.
VPN Server
The VPN server validates the credentials of all incoming VPN connections before allowing access to the intranet. Also, VPN servers perform decryption of incoming data and encryption of data outgoing from the intranet across the VPN server to another VPN client. The VPN server does not act as a routing gateway for the organization; therefore, access to/from the public internet does not pass through the VPN server unless the destination/source is a VPN client. The VPN solution supports the following features:
- User Authentication – VPN client authorization, authentication and accounting performed by digital certificates, Extensible Authentication Protocol (EAP), Transport Level Security (EAP-TLS) and Remote Authentication Dial-in User Service (RADIUS) server.
- Address Management – Allocation of private IP address to VPN client.
- Data Encryption – encryption and decryption with GRE/AH/ESP of VPN data carried over a public network.
- Key Management – generation of symmetric/asymmetric encryption keys for VPN client and server.
- Multiprotocol Support – support for public network protocols such as IP and Internetwork Packet Exchange (IPX).
Intranet VPN
A tunnel is configured between the two remote corporate locations to extend the intranet to provide a secure connection between branch offices. Since the two end-points are the same organization branches AAA functionality may be distributed or centralized.
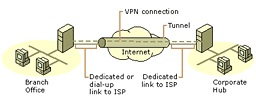
Access VPN
Access VPN provides individual users with remote access to the corporate private network. A Remote Access Server (RAS) is configured that performs VPN client authentication with a login password or an x.509 certificate. IPSec Key Exchange (IKE) creates master keys for user authentication and data encryption.
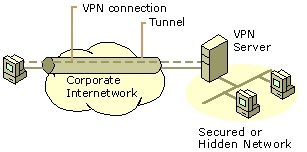
Extranet VPN
“If all the sites in a VPN are owned by the same enterprise, … e.g., in an intranet and in several extranets.”
The corporate intranet is extended to connect with another organization’s intranet via a VPN tunnel. Multiple users are allowed access to another end-point intranet across the VPN tunnel. This requires the configuration of multiple VPN connections in the same VPN tunnel. Since the two end-points are different agencies the user authentication mechanism must be agreed upon. Refer to figure 6, instead of the Branch office consider a business partner office.
